Nov 30, 2018 Version 1.9.5: Note: Ready for macOS 10.14 Mojave Fixed: Bug where Chrome Download Metadata wasn’t being identified for cleaning in some situations; Bug where Firefox Browsing History wasn’t being identified for cleaning in some situations.
macOS Mojave has a number of security and privacy enhancements that can help make using your Mac a simpler, safer, and more secure experience. Apple made changes to Safari, as well as expanded Gatekeeper and SIP services provided by the macOS.
Automatic Strong Passwords with Safari
Safari can automatically create strong 20-character passwords for you when you’re setting up a new service or account. Safari will populate the password and password confirmation field for you, though you can accept or reject the supplied password. The account password will be stored in Safari, and synced with your other Apple devices using iCloud. As long as you remain within the Apple environment (macOS, iOS, watchOS, tvOS), you can access all of your account passwords using just your Apple ID password.
To use Automatic Strong Passwords, launch Safari and browse to a website for which you would like to create a login account.
1) When you come to the password field, click or tap once in the field.
2) Safari will display a key icon in the far right edge of the password field.
3) Click or tap the key icon.
4) In the menu that appears, select Suggest New Password.
Privacy Scan For Mac Mojave 2017
5) A strong password will be generated.
6) You can click or tap in the password field, and select Use Strong Password, or Don’t Use.
Of course, to make the strong passwords easy to use, Safari can also auto fill login fields when needed:
1) Launch Safari and select Preferences from the Safari menu.
2) Select the Passwords item from the Safari preferences toolbar.
3) Place or remove the checkmark from the item labeled AutoFill user names and passwords.
Safari Password Reuse
Apple can’t put an end to password reuse, the practice of using the same password, or weak variants of a common password, over and over across multiple sites and services. Reusing passwords can be a disaster waiting to happen. Should someone gain access to one of your accounts, they’re going to try that same password with any other account or service they think you’re using.
As you can imagine, the results wouldn’t be very pretty if you’re reusing your passwords.
(Safari can audit your website passwords and point out when you reuse a password multiple times.)Safari in macOS Mojave won’t prevent you from reusing passwords on multiple websites, but it can warn you when you do:
Launch Safari, and then select Preferences from the Safari menu item.
In the Safari preferences window, select the Passwords item in the toolbar.
Enter the password for the current user in order to unlock the Safari passwords.
The passwords that Safari has remembered for you will be displayed. If any passwords are being reused, Safari will mark them with a yellow warning placard.
Clicking or tapping one of the warning symbols will display details about the warning, including where the password is being reused, and a link to the current site, so you can quickly go there and change the password.
Intelligent Tracking Prevention 2.0
High Sierra introduced Intelligent Tracking Prevention (ITP) to help prevent cross-site tracking, and reduce, or at least make the process very cumbersome, websites tracking your movements as you browse the web.
The original version of ITP used a 24-hour window to allow some cross-site tracking on the assumption that some web-based services would break if there were a complete elimination of cross-site tracking. An example of a site failing because of the inability to use cross-site tracking would be a banking or financial services site that uses persistent cookies to allow a login to a central server, which allows you to access multiple related services without having to log in to each individually.
ITP 2 removes the 24-hour window, and instead will throw a prompt up asking if you wish to allow a third-party site to access its stored cookies. Selecting Allow will let the third-party site access its cookies, as well as reset a 30-day timer, allowing another 30 days before those cookies are expunged. Selecting Don’t Allow will prevent the site from accessing the cookies this one specific time, and leave the 30-day timer intact, with no changes.
If you would like to find out more about ITP 1.x, the 24-hour, and 30-day timers, and how they’re used to assist in blocking cross-site tracking, check out the Rocket Yard article: How to Manage Cookies in Safari for High Sierra.
(Safari’s privacy capability includes an update to Intelligent Tracking Prevention that will warn you when third-party websites are attempting to access stored cookies.)You can turn cross-site tracking prevention on or off in the Safari preferences:
Launch Safari, and then select Preferences from the Safari menu.
In the preferences window, select the Privacy item in the toolbar.
Place or remove the checkmark from the box labeled Prevent cross-site tracking.
Fingerprinting Protection
Fingerprinting is a method that allows sites to build up enough information to be able to distinguish one computer from another that visits it. The site can do this without setting or using cookies. This “fingerprint” is obtained by examining the information the web browser is sending to the site, and comparing it to other fingerprints the site has already put together. Your Mac may be unique because of the fonts you have installed, the Safari extensions you’re using, the apps you have installed, social media status, and much more.
Find out more about fingerprinting in the article: What Secrets Your Browser Knows (and Reveals) About You.
Fingerprint protection seeks to make the information a site can gather more generic, making it more difficult to uniquely identify you. This is done in multiple ways:
- Allowing Safari to only list Apple-supplied system fonts installed, instead of any font that is present.
- Permitting a limited and simplified version of your system configuration to be sent.
- Preventing legacy Safari plug-ins from working, which prevents them from being used as markers in fingerprinting.
Fingerprint protection should help prevent your Mac from having a unique identity, though it may be some time before that goal is achieved. Right now, only a few days after the release of macOS Mojave, my Mac is seen as having a unique identifier at various sites that will test website fingerprinting (you can find a list of test sites at the link above). But I believe it’s the system configuration causing this; as more systems start upgrading to Mojave, the system should no longer be unique.
Safari Extensions and Plug-Ins
Support for legacy Safari extensions is removed with Mojave, and only extensions made available through the Mac App Store are supported. In addition, Mojave doesn’t support the old Netscape Plugin Application Programming Interface (NPAPI), which includes plugins such as Silverlight and Java.
Removing old plugins and only allowing extensions from the Mac App Store should help fortify Safari by eliminating them as possible malware attack vectors.
Security Changes: Gatekeeper and SIP
Gatekeeper takes on an expanded role in macOS Mojave. In its original incarnation, Gatekeeper allowed only apps that were signed or downloaded from the Mac App Store to run on a Mac (you could also turn Gatekeeper off). Later versions of Gatekeeper included the ability to isolate your data from apps that were attempting to access it.
In High Sierra, Gatekeeper protected Location Services, Contacts, Calendars, Reminders, and Photos. If an app or service needed information from any of those apps, you had to explicitly give it permission to do so. Mojave adds camera, microphone, and automation. Additionally, Gatekeeper controls access to Mail, Messages, iTunes, and Time Machine backups, as well as Safari browsing information, cookies, and call history, but does so under a group setting.
(Gatekeeper adds the capability to protect your Mac’s camera and microphone from surreptitious access by apps and services. It also protects additional data types, including Mail, Safari, and Time Machine, from unwanted access.)You can control how Gatekeeper works in the system preferences:
Launch System Preferences, and select the Security & Privacy preference pane.
Use the General tab to select where apps can be downloaded from (this is the original Gatekeeper control). You may need to unlock the lock at the bottom of the window to make any changes.
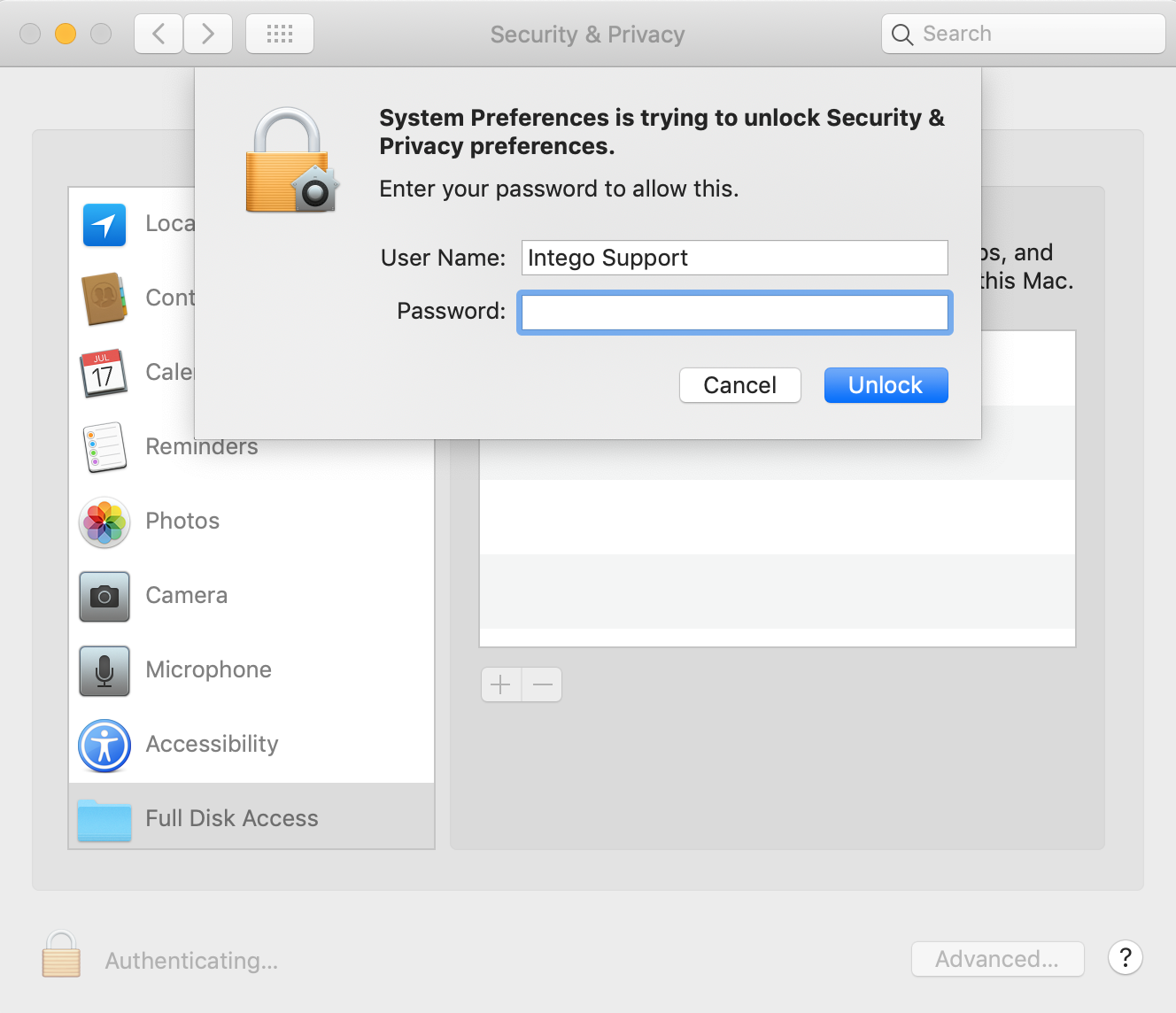
Use the Privacy tab to control which apps or services are allowed to access data from other apps. Select the app in the sidebar to see which apps have attempted to access data from the selected app. You can prevent, allow, or simply tweak how an app can access the data in the selected app.
The Full Disk Access item in the sidebar is a special group of apps and services that are controlled together. These include Mail, Messages, Safari, Home, iTunes, and Time Machine backups.
SIP Protection for Third-Party Apps
Apple has used SIP (System Integrity Protection) to protect system files, apps, and folders from being altered by third parties or by malware. With Mojave, SIP monitors system processes, and will stop any process from making alterations that are not allowed in its code signature, or any attempt to execute code that has not been signed by Apple.
The increased role SIP plays applies not only to system files and apps, but also to any apps or services that the system loads or launches. These changes should harden the Mac’s system from attack, or simply badly coded apps or services.
SIP in Mojave also offers some of its protective services to app developers, allowing them to use SIP to protect the integrity of their apps. SIP protection for apps is optional, and only the developer can make the choice to use SIP.
Notarized Apps
App notarization is another service offered to developers that can help protect your Mac from malware. Apple’s Notary service will examine ready-to-distribute application packages for the presence of any hidden malware, and that the app has been properly signed and uses SIP protection for apps.
If an app meets all the requirements, it will be notarized. When you launch a notarized app, it’s checked for any changes against the notarized version. If a difference is detected, a warning will be seen about possible malware, and a suggestion that the app should be trashed and the developer contacted
Security Code Autofill
Not really a security or privacy feature, more of a way to make two-factor authentication an easier process. When you set up your iPhone to forward SMS messages to your Mac (using the Mac’s Messages app), Mojave’s AutoFill feature will grab the security code from Messages and insert it into the security field on the Safari page. Mojave can also insert the security code into any app that has been upgraded to support Mojave’s Security Code AutoFill feature.
Wrap Up
Mojave brings many changes that make it a compelling update. For some of you, the security and privacy changes are a notable reason to upgrade. The ability to keep apps or services from accessing information you don’t want them to have, including using your camera or microphone, may be reason enough. For others, the changes to Safari may be just what you’re looking for to make password management easier, or to keep advertisers at bay.
Be Sociable, Share This!
Privacy Scan Mac
OWC is on-site wind turbine powered at 8 Galaxy Way, Woodstock, IL 60098 | 1-800-275-4576 | +1-815-338-8685 (International)
All Rights Reserved, Copyright 2018, OWC – Since 1988
My situation was I am sharing via SMB two Shares from a Mac running El Capitan
I was running this and connecting without an issue using a Mac Running High Sierra
I upgraded the Mac to Mojave and suddenly every time I tried to copy a file to or from the shares on th El Capitan Mac the finder would crash and the shares would drop ( mid copy ) ......
Privacy Scan For Mac Mojave California
Mojave Mac Os
I found a solution but a kind of odd way to fix it...
Privacy Scan For Mac Mojave Ca
I used an app called SMBconf ( you choose SMB version )......... chose to use SMB 3 on both Devices rebooted them both and Boom !! All working again .. I don't know if this just fixed a corrupted conf file ? but it worked for me !